Okay, I’m going to state the bleeding obvious – cybersecurity is really important. We all know that. But it is easy to become overwhelmed by the astronomical figures and the different types of cybersecurity threats which lurk in and outside of the workplace, the complex technology and a feeling of helplessness. The bad news is that cybersecurity aint gonna get any easier any time soon, the good news is that I have compiled 7 cybersecurity infographics that will help you understand the threat so that you can start to navigate these murky cybersecurity waters. Check out and share these 7 cybersecurity infographics with your colleagues:
1. Cybersecurity is a Big Deal
This is all about understanding the threat, and some of the everyday basic ways in which you can fall victim to a cyberscam. Ref: Stay Safe Online
2. Social Engineering – How YOU Can be Hacked
This cybersecurity infographic describes the basic and complex social engineering methods that maybe used. Ref: Smartfile
3. Phishing, Vishing & Smishing
You’ve probably heard of phishing, but have you heard of Vishing and Smishing…? Ref: Digital Guardian
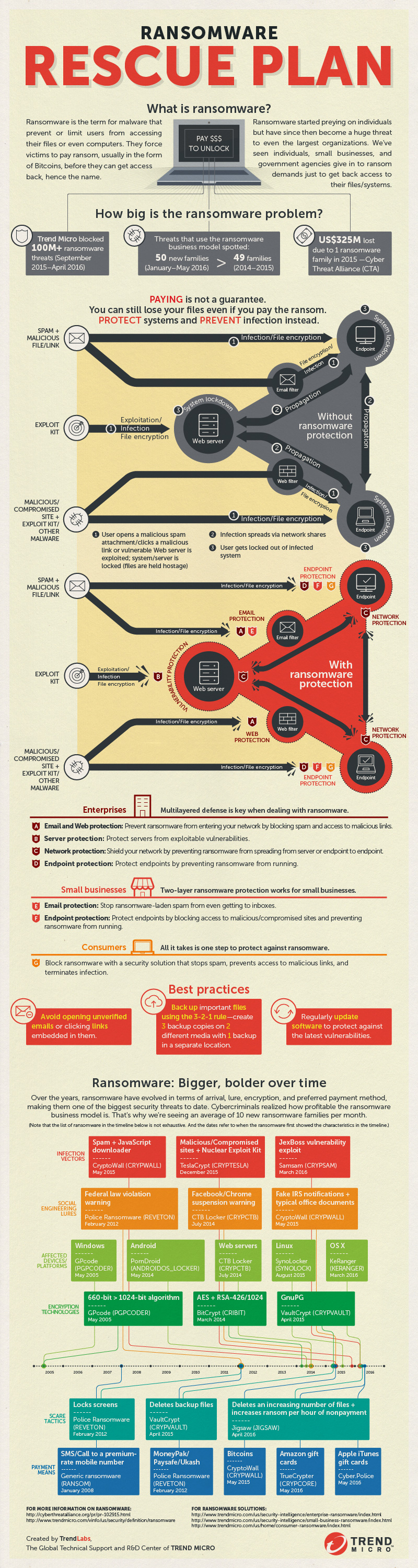
4. Don’t be Held to Ransom
The guys at Trend Micro have plenty of interesting security information – here they tackle Ransonware:
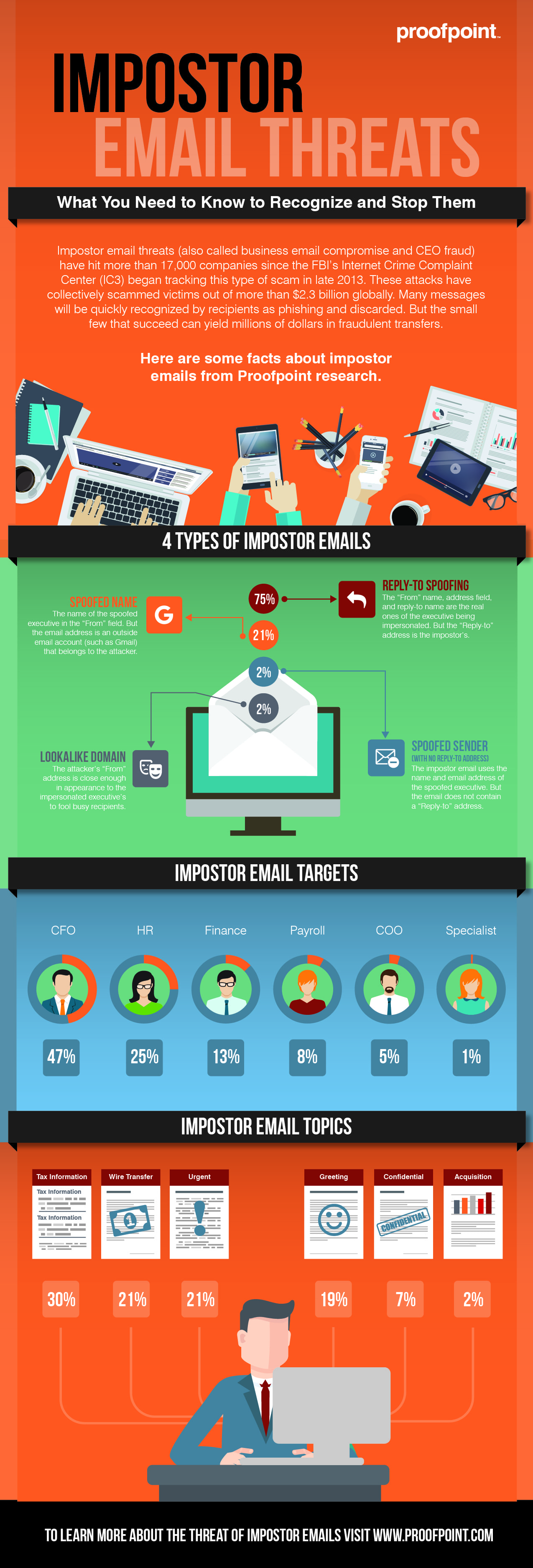
5. Business Email Compromise
I have talked about the CEO scam and business email compromise (BEC) in the past – this Proofpoint infographic provides a pretty cool overview:
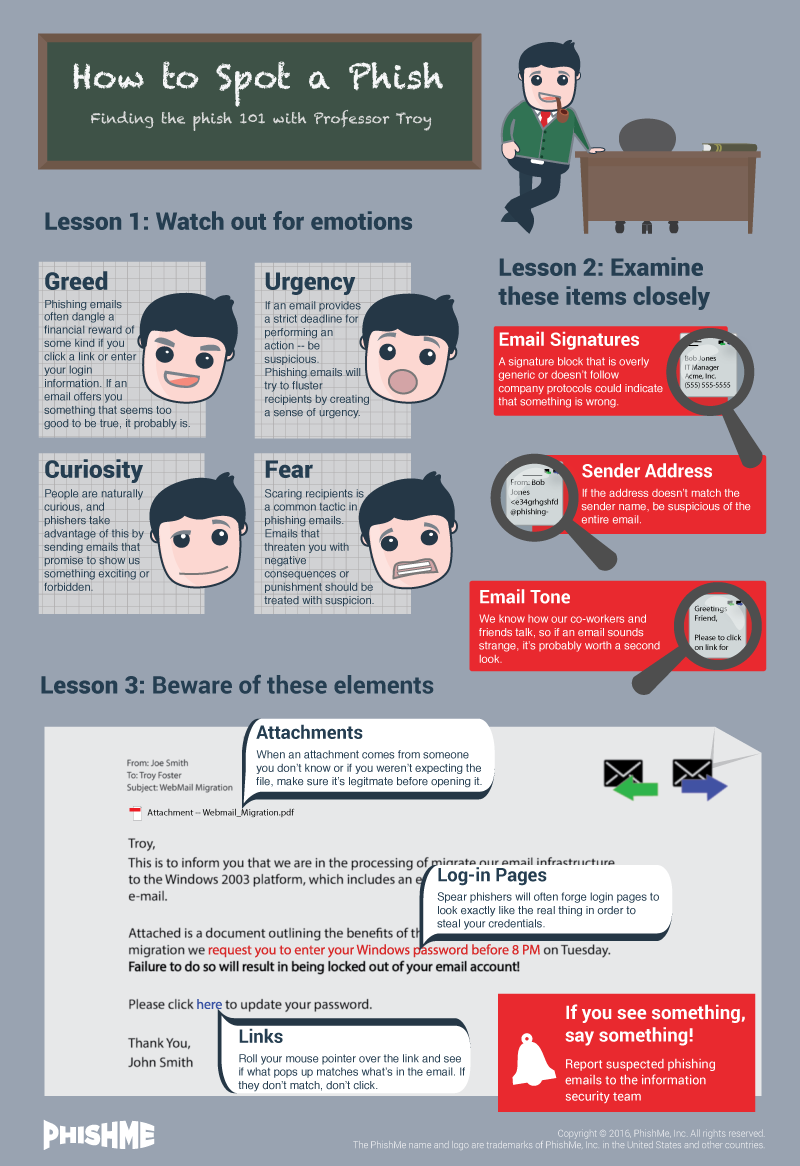
6. What to Look Out For:
As simple as this stuff sounds, people are still falling for it. Ref: Phishme
7. Are You The Weakest Link?
Lastly, cyber security is about continuous education. Ref: Trend Micro




Pingback: Digital Forensics EXPLAINED In a Kick-Ass Infographic!